After Configuring The Clearpass With Cisco Switch For Mac
Switch(config)# interface fa0/1 Switch(config-if)# switchport port-security Switch(config-if)# switchport port-security maximum 1 Use the switchport port-security command to enable port-security. I have configured port-security so only one MAC address is allowed.
Once the switch sees another MAC address on the interface it will be in violation and something will happen. I’ll show you what happens in a bit Besides setting a maximum on the number of MAC addresses we can also use port security to filter MAC addresses. You can use this to only allow certain MAC addresses. In the example above I configured port security so it only allows MAC address aaaa.bbbb.cccc. This is not the MAC address of my computer so it’s perfect to demonstrate a violation. Switch(config)# interface fa0/1 Switch(config-if)# switchport port-security mac-address aaaa.bbbb.cccc Use the switchport port-security mac-address command to define the MAC address that you want to allow.
Now we’ll generate some traffic to cause a violation: C: Documents and Settings H1 ping 1.2.3.4 I’m pinging to some bogus IP addressthere is nothing that has IP address 1.2.3.4; I just want to generate some traffic. Here’s what you will see: SwitchA#%PM-4-ERRDISABLE: psecure-violation error detected on Fa0/1, putting Fa0/1 in err-disable state%PORTSECURITY-2-PSECUREVIOLATION: Security violation occurred, caused by MAC address 0090.cc0e.5023 on port FastEthernet0/1.%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to down%LINK-3-UPDOWN: Interface FastEthernet0/1, changed state to down We have a security violation and as a result the port goes in err-disable state. As you can see it is now down. Let’s take a closer look at port-security: Switch# show port-security interface fa0/1 Port Security: Enabled Port Status: Secure-shutdown Violation Mode: Shutdown Aging Time: 0 minsAging Type: Absolute SecureStatic Address Aging: Disabled Maximum MAC Addresses: 1 Total MAC Addresses: 1 Configured MAC Addresses: 1 Sticky MAC Addresses: 0 Last Source Address:Vlan: 0090.cc0e.5023:1Security Violation Count: 1 Here is a useful command to check your port security configuration. Use show port-security interface to see the port security details per interface. You can see the violation mode is shutdown and that the last violation was caused by MAC address 0090.cc0e.5023 (H1).
Switch# show interfaces fa0/1 FastEthernet0/1 is down, line protocol is down (err-disabled) Shutting the interface after a security violation is a good idea (security-wise) but the problem is that the interface will stay in err-disable state. This probably means another call to the helpdesk and you bringing the interface back to the land of the living! Let’s activate it again: Switch(config)# interface fa0/1 Switch(config-if)# shutdown Switch(config-if)# no shutdown To get the interface out of err-disable state you need to type “shutdown” followed by “no shutdown”. Only typing “no shutdown” is not enough! It might be easier if the interface could recover itself after a certain time. You can enable this with the following command.
Hi Rene, I have a strange problem related to your post. We have a unmananged switch connected to a managed switch port. That port is configured as follows: description Conference Room switchport access vlan 43 switchport mode access switchport port-security maximum 16 switchport port-security authentication host-mode multi-host authentication port-control auto dot1x pae authenticator dot1x timeout quiet-period 20 dot1x timeout tx-period 10 spanning-tree bpduguard enable If a user connects to this switch and then unplugs (not Logoff), goes to their d. Hello Hussein.
In order to clearly answer this question, we have to define two different functionalities of the switch: port security and the MAC address table. Port security has been explained well in this lesson, so I’ll just mention that port security allows only devices with specific MAC addresses to connect and function on a specific interface.
The MAC address table is a table that records MAC addresses and the corresponding interface on which they can be found. This table exists to give a switch it’s most basic function which also distinguishes it from a. Hello Hussein. That’s a very good point, and yes, it requires clarification. In order for port security to function, the “allowed” MAC addresses are configured for each port. These are the secure addresses. Now there are several ways a switch can learn these addresses: Statically or dynamically.
The statically configured MAC addresses for port security DO NOT age out. They are permanent. These are the addresses that are configured using the command: switchport port-security mac-address 1000.2000.3000 The switchport port-security aging time command only aff. Great stuff here at NetworkLessons.com! Rene's lessons are real world scenarios which allow us to grasp most of the networking concepts with ease and on a fast track. The discussion forums that follow each tutorial allow us to comprehend technical nitty gritty's in a clear and precise manner.
I have learned most of the routing and switching concepts on a fast track here which is otherwise not possible via text book learning. I recommend NetworkLessons.com to all networking professionals. Aravind Chinapaga Sr. Associate Network Engineer August 25, 2016. As a CCNP Switch 300-115 student, I want topics described and explained in simple, concise and brief terms. Rene does just that!
No frills, no waffle.just facts! I like the way he builds on topics, taking you from beginning, intermediate to advanced material. If I need to go back to basics or revisit a forgotten topic, I can access all the CCNA material on the site. I find this an excellent resource: CCNA, CCNP all in one place. It's an excellent site for revision. Rene himself is accessible if needs be. You can copy the printed material and it pastes perfectly formatted into word.
In terms of training material, this is by far the best value for money on the net. Seamus Keane Support Engineer CCNA September 10, 2015. NetworkLessons.com is a fantastic teaching platform. Every lesson is set up in a way that makes learning interesting and fun. Rene is an expert and doesn't try to impress his readers on how much he knows. He has a genuine desired to help others to grasp all network concepts.
The one aspect I enjoy the most are the live demonstrations he includes with each lesson. The labs presented in his lessons are easily reproducible in GNS3 which has allowed me to hone my skills. NetworkLessons.com is very affordable and should be a part of anyone's Network Training Library. Paul Lagatta Network Engineer September 1, 2016. As I study for my CCIE I read a lot of books, blogs and technotes about the individual topics to try to ensure that I have a complete understanding of each subject. Networklessons.com is by far the best at breaking down complex items into easily understood pieces, and it is my go-to website when I'm getting confused about something. If when I get my CCIE, I will owe Rene a personal thank you for the assistance and the online resources of Networklessons.com!
Dylan Costigan Network Engineer January 18, 2016. Networklessons.com explains networking clear, and keeps it simple & clean. It was a great help for designing one of our clients DMVPN network setup. Rene also took a step forward in helping me answering all my queries personally with respect to my network design & set-up. I am one of the happiest members because I know I have Networklessons.com when I require any relevant information, which shows their expertise in the networking. Thanks again Rene for all your brilliant work and keep up the good work! Ramasubbiah Network Engineer March 12, 2016.
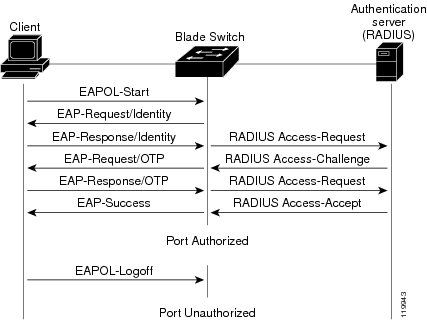
802.1x Integration with Active Directory 7 Dec 2006 Filed in The idea behind is to provide Layer 2 authentication; that is, to authenticate LAN clients at the Ethernet layer. (This is before the client gets a DHCP lease or anything of that nature.) With 802.1x in place, rogue users can’t just tap into a physical connection on the network. In order to gain network connectivity, the device must authenticate before network traffic is allowed.
The idea here is to configure 802.1x authentication on a network switch in such a way as to leverage the existing authentication infrastructure provided by Active Directory. Like it or not, Active Directory is a widely deployed directory service and leveraging it where we can will certainly provide an advantage. This process uses RADIUS to provide an interface between a Cisco Catalyst 3560G switch (the 802.1x authenticator in this scenario) and Active Directory. I could only test as the client (or 802.1x supplicant), but I’m confident that the configuration will work equally well with. Configuring the Cisco Catalyst 3560G The Catalyst switch I used in this configuration was running IOS 12.2(25); please note that the commands listed here may be different in different versions of IOS. To configure the switch for 802.1x authentication, three steps are involved:.
Enable 802.1x authentication on the switch (global configuration). Configure the RADIUS server(s) to which the switch will communicate for authentication requests. Enable 802.1x authentication on the individual ports. ( from the was tremendously helpful in configuring 802.1x.) First, to enable 802.1x authentication on the switch, use the following commands in global configuration mode: aaa new-model aaa authentication dot1x default group radius aaa authorization network default group radius dot1x system-auth-control This enables 802.1x globally on the switch, but none of the interfaces are enabled for 802.1x authentication.
Next, we configure the RADIUS server(s) to which the switch will pass the 802.1x authentication traffic. That’s handled with these commands in global configuration mode: radius-server host 10.1.1.254 auth-port 1645 acct-port 1646 key Password (This should all be on one line.) Note that the “auth-port” and “acct-port” parameters are only necessary if you are using nonstandard ports. Since Microsoft’s IAS (Internet Authentication Service, which provides the RADIUS interface to Active Directory) uses both sets of standard ports (1645/1812 and 1646/1813) you won’t need to specify these parameters. The “key” parameter is a shared secret key between the RADIUS client (the switch) and the RADIUS server. Obviously, you’ll want to use something other than “Password”. Finally, to enable 802.1x on the applicable interfaces, you’ll use these commands in interface configuration mode (replace gi0/23 with the interface you want to configure): int gi0/23 dot1x port-control auto That enables 802.1x authentication on that specific port.
Repeat the process for all ports that should use 802.1x authentication. Note that some ports can’t be enabled for 802.1x authentication; most notably, trunk ports can’t be used for 802.1x. Refer to the Cisco documentation (or the documentation from your particular vendor) for complete details on the limitations.
Now that the switch is configured, we move on to configuring Active Directory. Configuring Active Directory and IAS I suppose that saying we need to “configure Active Directory” isn’t entirely accurate, since no configuration changes and no schema extensions are necessary to make this work.
All that really needs to be done is to enable reversible password encryption (which can be done on a per-user basis) and setup Internet Authentication Service (IAS). First, regarding reversible password encryption: The configuration described here uses MD5 hashes (passwords) to authenticate clients to the network. There are other methods, such as digital certificates, to accomplish the same thing, and I’ll probably revisit this configuration again at a later date to look at using those. For now, though, the use of MD5 for authentication means that we have to enable reversible password encryption for every user that will need to authenticate via 802.1x, and those users will need to change their passwords after that change is made.
A pain, yes, and a potential security concern, yes, but necessary at this point. (I won’t bother going through the details of enabling reversible password encryption here; there are plenty of resources available on the Internet, like, that provide that information.) Configuring IAS is really pretty straightforward. I’ve discussed the use of IAS before (here in discussing and here regarding ), and I’ll refer you back to those articles for some of the basics on setting up and configuring IAS.
To configure IAS in this instance (once it has been installed and registered with Active Directory), we’ll do the following:. Add the Cisco Catalyst switch as a RADIUS client. We’ll need to be sure to specify the same shared secret as used in the switch configuration. We’ll create a new remote access policy. The conditions on the policy should be “NAS-Port-Type” (set to Ethernet) and “Windows-Groups” (set to whatever group should be allowed to authenticate via 802.1x; I used Domain Users). The profile associated with this policy should be edited to note only the EAP MD5 authentication type (under “EAP Methods” on the Authentication tab); all other authentication types should be unchecked.
In addition, all encryption types on the Encryption tab should be unchecked except for “No encryption”. At this point, the IAS configuration should be complete. Now for the final step: configuring the client to use 802.1x. Configuring the Client (Mac OS X) As mentioned earlier, I didn’t have a physical Windows XP Professional-based machine to test with, but I did do some testing with Mac OS X. Although the software used to configure the operating system is different, the overall configuration is similar and should work without any major hitches on Windows XP.
This item will be shipped through the Global Shipping Program and includes international tracking. Back to home afw 4300b. Mgi p65 mdde128f drivers for mac.
After Configuring The Clearpass With Cisco Switch For Mac Download
To configure Mac OS X, launch the Internet Connect software in the Applications folder and follow these steps:. From the File menu, choose “New 802.1X Connection”. Specify a description and choose the appropriate network port (typically “Built-in Ethernet”). Specify a username and password. For authentication types, click to enable MD5 and move it to the top of the list.
Uncheck all other authentication types. Click OK to save the connection. Once the connection has been defined, you can plug your OS X-based system into one of the 802.1x-enabled ports and click “Connect” in the Internet Connect window.
If everything is configured correctly, you should be connected and be able to pass network traffic without any issues. If things don’t work, go back and check the switch configuration and the logs on the IAS/RADIUS server. In particular, the logs may indicate that an incorrect password was used, or you may be able to determine that the switch isn’t even talking to the IAS/RADIUS server (perhaps a typo in the server address?). By the way, configuring Mac OS X to use 802.1x for wireless connections is equally easy and done the same way (using Internet Connect). I used to regularly use my in an environment that used 802.1x and EAP-FAST/LEAP for wireless authentication with no problems. Future enhancements to this configuration include switching from EAP-MD5 to something like EAP-TLS or PEAP; this will avoid the need to enable reversible password encryption on the domain. Metadata and Navigation Previous Post: Next Post: Be social and share this post!